Download Your Guide to Penetration Testing as a Service (PTaaS)
Download the PDF or Scroll Down for the Interactive Version
Security isn’t a one-time event, it’s a continuous process. Our white paper, Your Guide to Penetration Testing as a Service (PTaaS), explores how ongoing, expert-led security testing can help you uncover vulnerabilities faster, reduce remediation times, and shift from reactive to resilient.

Learn the difference between true PTaaS and other solutions like crowdsourced cybersecurity and on-demand testing, plus see what you should look for in a PTaaS provider.

Discover how continuous penetration testing reveals vulnerabilities in real time, helping your team remediate faster and reduce exposure.

See how TrollEye Security’s PTaaS combines automated scans, expert validation, and enhanced remediation management to drop critical findings to near-zero.

Executive Overview
Penetration Testing as a Service (PTaaS) is an emerging approach that offers continuous penetration testing, integrating security into daily operations. Unlike traditional, periodic testing, PTaaS provides real-time insights into vulnerabilities, enabling security teams to respond swiftly to potential threats.
Why PTaaS Is Essential Today
Today’s cybersecurity challenges demand more than one-off testing and disjointed tools. Traditional approaches to vulnerability management often leave gaps, fragmented processes, long remediation cycles, and limited visibility. Penetration Testing as a Service (PTaaS) is the answer to these shortcomings.
PTaaS takes your cybersecurity program to the next level by transforming penetration testing from a periodic checkbox exercise into a continuous, intelligence-driven operation. With integrated tooling, real-time reporting, and professional support, PTaaS empowers organizations to proactively identify, prioritize, and remediate vulnerabilities before they’re exploited.
In the sections that follow, we’ll explore the foundational features that define true PTaaS, how it differs from legacy testing methods, the measurable benefits it delivers to your team, and our own unique PTaaS process.

According to Gartner®, by 2028, remediation cycles will be twice as fast in organizations using PTaaS compared to those dependent on manual testing approaches.
Gartner, Innovation Insight: Penetration Testing as a Service, Mitchell Schneider, Dhivya Poole, Carlos De Sola Caraballo, William Dupre, Eric Ahlm, 3 October 2025
Gartner is a registered trademark of Gartner, Inc. and/or its affiliates and is used herein with permission. All rights reserved.

What Penetration Testing as a Service (PTaaS) Isn't
Before we move on to the benefits of Penetration Testing as a Service (PTaaS), it’s important to clarify what PTaaS isn’t. Not every offering labeled “PTaaS” delivers the consistent, integrated, and expert-driven approach that defines a true service.
Penetration Testing as a Service (PTaaS)

Trusted, vetted security professionals.

Continuous engagement and clear accountability.

Deep contextual knowledge built over time.
Vs
Crowdsourced Cybersecurity

Inconsistent tester quality.

Lack of accountability or long-term partnership.

Lack of deep understanding of your environment.
Penetration Testing as a Service (PTaaS)

Recurring testing as part of an ongoing security lifecycle.

Historical insights and trend tracking for smarter remediation.

Proactive identification and prioritization of risks.
Vs
On-Demand Penetration Testing

One-off assessments with no follow-up.

No context or history of previous tests.

Reactive rather than proactive.
Penetration Testing as a Service (PTaaS)

Expert-led analysis to find logic flaws and business logic vulnerabilities.

Actionable, validated findings with remediation guidance.

Emulates real-world threat actor tactics and techniques.
Vs
Automated Penetration Testing

Lacks human context and validation.

High false positives, low actionable insight.

Can’t simulate real-world attacker behavior.

The Foundational Features of PTaaS You Should Expect
There are a few foundational features that you should look for in every PTaaS solution. Here is what you should look for when considering PTaaS;

Continuous Security Testing
All PTaaS solutions should offer continuous scheduled penetration testing, ensuring that new vulnerabilities are detected and addressed promptly.

Scalability
PTaaS should easily scale to meet business demands, whether they're assessing a single application or an entire enterprise environment.

Cost-Effectiveness
By adopting a PTaaS solution, you should be able to save the cost associated with purchasing separate tooling, hiring staff to manage that tooling, and hiring a vendor to conduct an annual penetration test.

Expertise
Make sure that your PTaaS provider uses a team of experts who are knowledgeable about the latest cyber threats and vulnerabilities, ensuring a high testing standard.

Centralized Platform
Your chosen solution should include a robust platform that provides real-time reporting and allows you to easily manage findings and track remediation.


Advanced PTaaS Features You Also Need to Stay Ahead of Threats
Not all PTaaS offerings are created equal. To ensure your organization is fully protected, it’s essential to leverage features that go beyond standard testing. Our Penetration Testing as a Service (PTaaS) stands out by incorporating advanced capabilities that provide a more comprehensive and proactive approach to cybersecurity, addressing critical threats and compliance requirements.
These advanced features are critical for any organization looking to stay ahead of sophisticated cyber threats and achieve a robust, future-proof security posture.

Using Dark Web Credentials in Testing
We provide you with monthly scans of the dark web through our platform to uncover stolen or compromised credentials associated with your organization. This feature also enables you to monitor third-party vendors and executive data exposure, reducing the risk of credential abuse or targeted attacks.

Attack Surface Management (ASM)
We provide continuous visibility into your entire attack surface, external, internal, and on-premises. By identifying exposed services, misconfigurations, unauthorized systems, and changes across your environment, ASM ensures nothing slips through the cracks.

Phishing Assessments
We conduct our phishing simulations on a quarterly basis, crafting scenarios specific to your business environment and challenges. These campaigns provide insight into vulnerabilities in your human firewall, preparing your team against real-world phishing attacks.
A Powerful Process
Our effective Penetration Testing as a Service (PTaaS) follows a clear and continuous five-step process: Pen Testers Assess vulnerabilities, Pen Testers Prioritize risks, the Client Acts on findings, Pen Testers Re-Assess improvements, and Processes Improve over time.
This ongoing cycle, conducted on a weekly or monthly basis, provides organizations with a continuous and comprehensive view of their security posture, ensuring threats are addressed promptly and defenses are consistently strengthened.
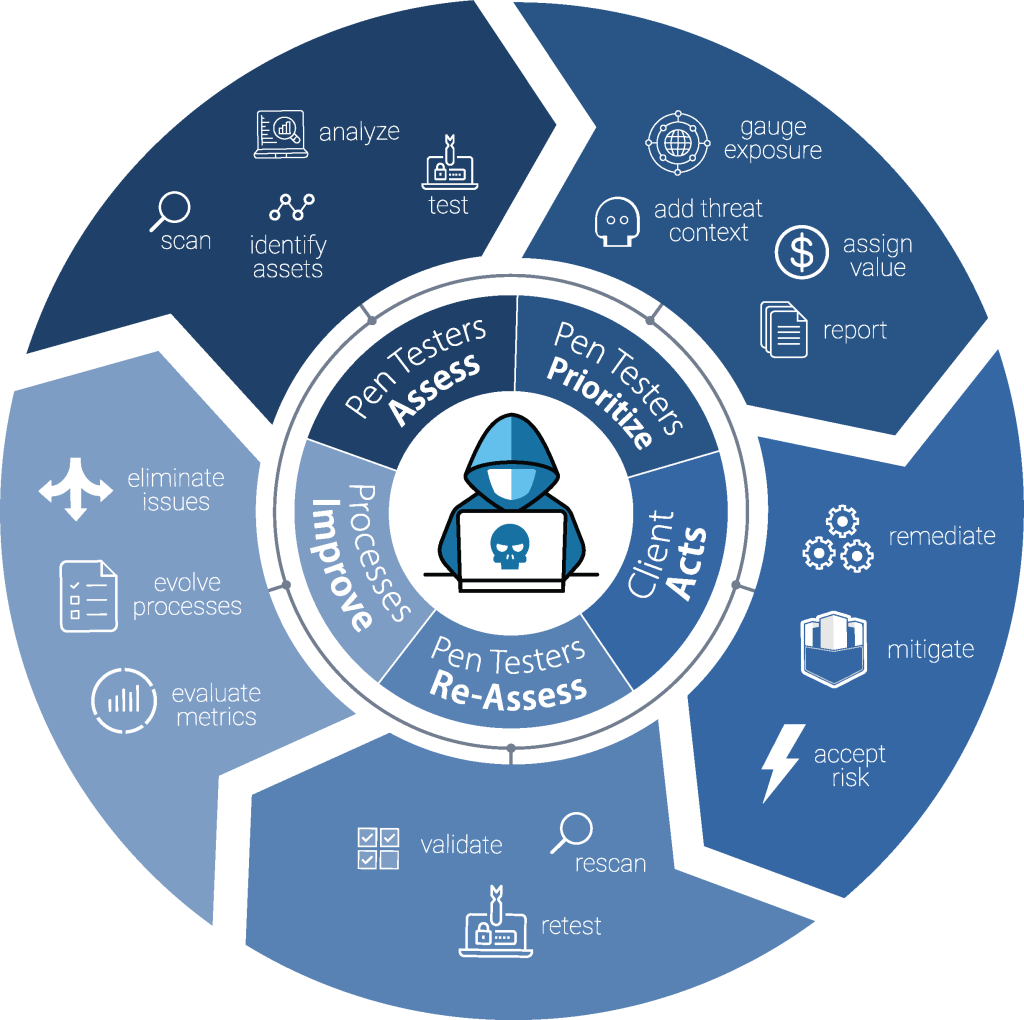
Step 1: Pen Testers Assess
Our process begins with a thorough scan of your systems using our platform, identifying valuable digital assets such as databases and applications alongside any vulnerabilities that could be exploited by attackers.
Once vulnerabilities are detected, an in-depth analysis evaluates their nature, potential impact, and associated risks.

Scan

Identify Assets

Analyze

Test
Step 2: Pen Testers Act & Prioritize
Once vulnerabilities are identified and tested, we begin by adding real-world threat context, mapping each issue to known attacker tactics and active threats in the wild. We then gauge exposure by assessing how accessible the vulnerability is, who could exploit it, and what systems would be affected.
Based on this analysis, we assign a value to each finding, prioritizing issues by actual risk to your business. All of this is delivered through our platform, giving your team real-time visibility into risks, so they can act without delay.

Add Threat Context

Gauge Exposure

Assign Value

Report
Step 3: Client Acts
With a clear understanding of the vulnerabilities and their priority, your team is empowered to take action. You can remediate the most critical issues, ensuring they are fully resolved to prevent exploitation, or mitigate vulnerabilities that present high risk by reducing their impact or likelihood. In some cases, after thorough analysis, you may choose to accept certain low-risk vulnerabilities based on the potential cost of remediation.

Remediate

Mitigate

Accept Risk
"I consider TrollEye to be a true hidden gem in the realm of security solutions and an invaluable technology partner. Talquin has been utilizing TrollEye's services for over four years now, and our experience has been nothing short of exceptional."

Step 4: Pen Testers Re-Assess
Once remediation or mitigation steps are taken, our team conducts a rescan of your systems to confirm that the vulnerabilities have been addressed. A retest is then performed to validate that all issues have been effectively resolved and that no additional security concerns have been introduced during the remediation process. This validation step ensures that your organization’s defenses are back to full strength and that no new vulnerabilities have emerged.

Re-scan

Re-test

Validate
"PTaaS has been a wonderful addition to our development lifecycle, and TrollEye’s platform provides a unique experience with excellent value!"

Step 5: Process Improvements
After the reassessment and retesting, any lingering issues are eliminated, and the findings are used to improve your organization’s overall cybersecurity processes. By incorporating lessons learned from each assessment, your defenses evolve to better protect against future threats. We also evaluate key performance and risk metrics to track the ongoing effectiveness of your security measures, ensuring continuous improvement in your cybersecurity posture over time.

Evaluate Metrics

Evolve Processes

Eliminate Issues


The Clear Benefits of Our PTaaS
By combining continuous testing, role-based vulnerability distribution, and regular cadence meetings, our Penetration Testing as a Service (PTaaS) offering drives faster, more effective remediation. As a result, engaged clients see critical and high-severity findings drop to nearly zero within six months of onboarding, transforming their security posture from reactive to resilient.
"Our clients see critical and high findings drop to almost zero within six months of starting PTaaS."

Test Your Systems Up to Weekly

Consistently Improve Your Security Strategy

Distribute Vulnerabilities Based on Role

Take Your Security to the Next Level

The TrollEye Security Advantage You Need
We deliver a blend of rigorous real-world testing, expert insight, and long-term partnership, ensuring organizations are fortified against both current and emerging threats, making us a standout choice in the PTaaS arena.

True Continuous Testing
TrollEye Security delivers real penetration testing on a continuous schedule, not automated scans or one-off engagements labeled as “PTaaS.” With monthly or weekly testing, we’re able to uncover new vulnerabilities as your environment changes, validate past remediations, and help your organization make consistent progress toward reducing risk.

Ongoing Partnership
We operate as an extension of your team. Through regular cadence meetings, we help prioritize remediation, strengthen your internal processes, and track improvement over time. Our long-term engagement model results in fewer critical findings, better collaboration, and a more mature security program.

Our Centralized Platform
All testing activities, validated findings, and remediation workflows are managed through our centralized platform. It gives your team full visibility into test progress, timelines, and trends, while enabling faster remediation through a Kanban interface and role-based distribution, so you can manage everything from one location.

Extended Risk Visibility
Our PTaaS offering includes more than just penetration testing, it also includes attack surface management, dark web analysis, and phishing assessments. By combining these elements, we help you identify risks that others miss, from exposed assets and leaked credentials to human vulnerabilities, giving you a more complete and actionable view of your security posture.

Get Your Demo
Discover how our PTaaS offering gives your security team the tools, information, and guidance they need to strengthen your defenses by reaching out and scheduling a thirty-minute discovery call today.
Contact Us Now:

(833) 901-0971

