Dark Web Analysis
We Are Your Eyes on The Dark Web
Stolen credentials remain one of the most common entry points for attackers, but most dark web monitoring tools stop at simply alerting you that credentials have been found. They don’t tell you which ones matter, whether they’re still active, or how they could be used against your organization. That leaves your team with limited context and no clear path forward.
Our Dark Web Analysis goes further. With monthly scanning and hands-on validation by our penetration testers, you’ll know exactly which credentials are exposed, whether they’re actionable, and what a threat actor could do with them.

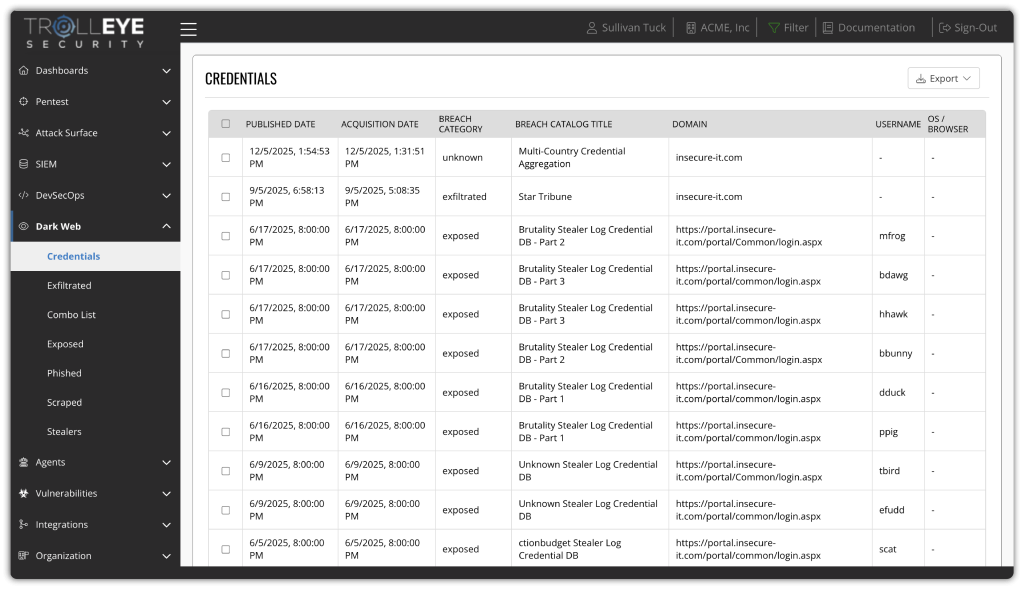
Gain Visibility Instead of Noise with Dark Web Analysis
The dark web serves as a marketplace for stolen data, malicious tools, and illegal services, posing a significant threat to organizations of all sizes. Our Dark Web Analysis service is designed to help you stay ahead of these threats by providing continuous, comprehensive monitoring and proactive measures to protect your valuable assets.
By leveraging our advanced dark web monitoring capabilities and expert analysis, we provide your organization with critical insights into potential vulnerabilities and breaches before they escalate. Our service ensures that your credentials, sensitive data, and organizational information are not being exploited by malicious actors.

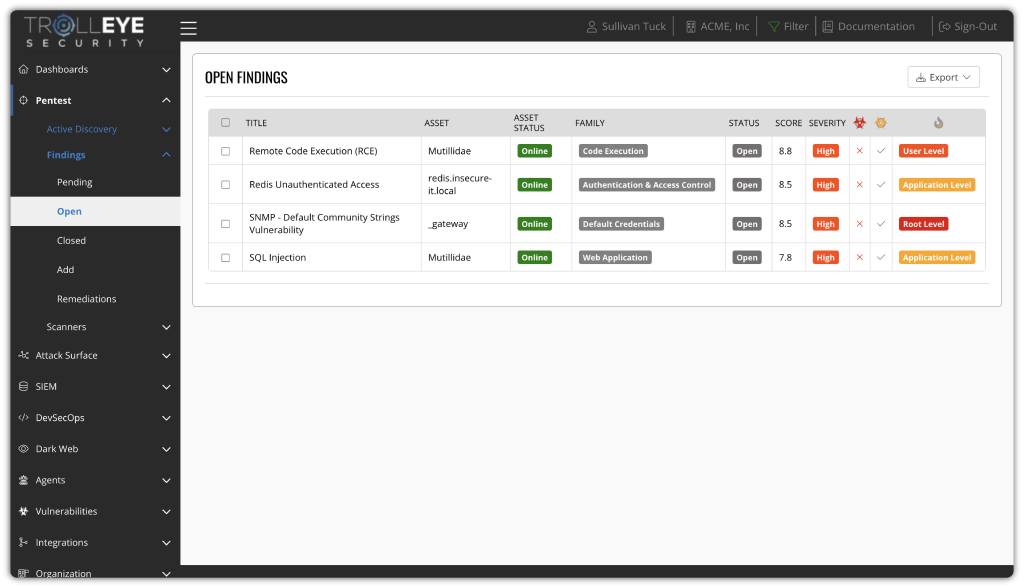
Rapid Account Takedown for Exposed Credentials
Identify exposed credentials tied to your organization and take action before they’re exploited. We help validate risk, prioritize affected users, and close compromised accounts quickly to reduce the likelihood of account takeover, lateral movement, and ransomware access.

Trend Analysis for Ongoing Exposure Reduction
Track how your organization’s exposure changes over time across credentials, domains, and data leaks. By identifying recurring patterns and high-risk behaviors, you gain insight into root causes and can strengthen controls where breaches and credential reuse are most likely to occur.

Active Malware and Infostealer Campaign Detection
Detect malware, infostealer activity, and credential harvesting operations targeting your environment. This intelligence adds real-world context to your security program, enabling faster response and more accurate prioritization of defensive controls.
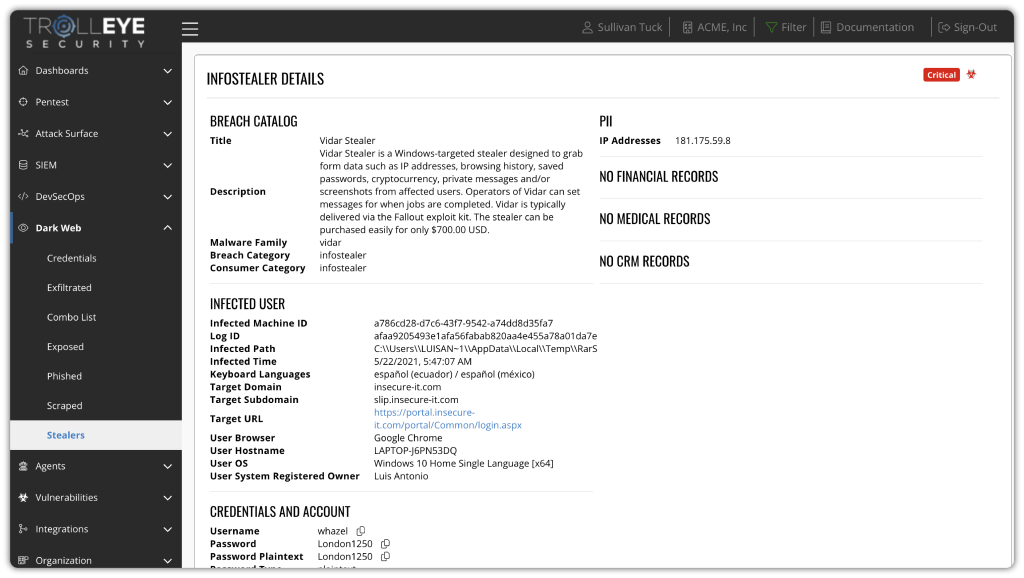
Credential Validation Through Continuous Security Testing
Turn dark web intelligence into action by safely validating exposed credentials during authorized security testing. This allows your team to confirm real-world impact, strengthen detection, and remediate weaknesses before attackers can exploit them.
Dark web knowledge is power. Schedule your demo and see how exposed your organization is today.

TrollEye Security: Taking Dark Web Protection To The Next Level With Expert Analysis
Dark web monitoring is the process of scanning the hidden parts of the internet to detect and alert organizations about the presence of their sensitive data, such as personal, financial, or corporate information. However, mere monitoring of the dark web isn't enough; what sets our offering apart is the comprehensive analysis of dark web findings.
Although we do monitor the dark web for your stolen and compromised credentials, we don't just scan for credentials, we analyze them. Doing this allows us to find out which ones are actionable, enabling you to change any jeopardized credentials swiftly, keeping your organization safe.
FAQs
What’s Dark Web Analysis?
Dark Web Analysis is a continuous cybersecurity service that monitors dark web marketplaces, forums, and leak sites for threats tied to your organization. It identifies compromised employee credentials, breach records involving third-party vendors, and exposed personal data of executives. This intelligence is delivered directly to your security team, enabling them to secure accounts, assess vendor risk, and protect high-value individuals from targeted attacks.
How is this different from basic dark web monitoring?
Basic dark web monitoring tools rely entirely on automated scraping and often return noisy, unverified results. Our Dark Web Analysis goes beyond that. Every alert is manually validated by our analysts, reducing false positives and ensuring the exposures we report are accurate, actionable, and prioritized by risk. We also provide context, such as when the data was leaked, how it was obtained, and whether credentials are still active, so you can take targeted action.
What types of threats do you detect?
We identify and analyze a wide range of threats, including:
- Leaked credentials related to your organization including executives, employees, and customers.
- Credential reuse across multiple breaches and platforms.
- Passwords stored in plaintext or weakly hashed formats.
- Exposure of confidential documents, internal systems, and proprietary data.
- Vendor and partner exposures that could impact your attack surface.
Do you provide remediation recommendations?
Yes, every alert comes with clear, actionable guidance based on the nature of the exposure. For example:
- If a password is exposed and still in use, we recommend a forced reset and review of other systems where it may have been reused.
- If a third-party breach is detected, we help assess your exposure and recommend security actions like MFA enforcement or vendor escalation.
Our cadence meetings also provide a space to walk through exposures, prioritize response, and track risk reduction over time.
Can we monitor more than one domain or brand?
Absolutely, our Dark Web Analysis solution supports multi-domain monitoring, making it ideal for holding companies, multinational organizations, or those managing multiple brands or subsidiaries. You can configure each domain or brand independently and receive reports that segment data accordingly.
Learn More About Dark Web Analysis
Use our latest resources from articles to white papers to learn more about what Dark Web Analysis is, and how it gives your security team the information, tools, and guidance they need to secure your organization.

Download Your Guide to Dark Web Analysis
Learn how Dark Web Analysis goes beyond traditional monitoring and gives your security team insights into stolen credentials, vendor risk, and executive exposure.
The Next Best Thing to Cyber Time Travel
Along with our penetration testing, or “pen testing” services, our dark web analysis offers an additional layer of security by determining whether or not you’ve already experienced a breach. TrollEye Security can help you reduce your future risk by testing the strength of your current measures, but we can also help you stop damage that’s already been done by discovering what previously exposed data you need to lock down. No one can go back in time and undo what’s already been done, but we can help plug the leak.

Make Your Cybersecurity Air Tight
When it comes to securing sensitive data, many companies think firewalls and anti-virus protection are enough. It’s only after they experience a hack that they discover these defensive measures are only enough to deter amateur cyber criminals. With attacks becoming more sophisticated every year, the best defense is a good offense. When you use internal and external penetration testing, continuous penetration testing, physical penetration testing, and social engineering assessment services for your cyber risk management, you’re taking the most aggressive stance possible against cybercrime.
No level of exposed data is acceptable for your critical business information. Fortunately, you don’t have to be a victim. You can reduce your risk with actionable intel from TrollEye Security. Call us today for your free initial consultation.

