Understanding Distributed Denial-of-Service (DDoS) Attacks
When it comes to maintaining a profitable business or running a successful organization, availability is everything. Whether it’s a bank’s online portal, a hospital’s patient management system, or a retailer’s e-commerce platform, even minutes of downtime can lead to major financial losses and erode customer trust. That’s exactly what makes Distributed Denial-of-Service (DDoS) attacks so destructive.
A DDoS attack overwhelms a target’s infrastructure with an enormous flood of malicious traffic, rendering legitimate users unable to access services. While early DDoS incidents relied on rudimentary botnets and brute-force methods, modern campaigns are far more sophisticated, requiring security teams to adopt strong layered defenses that keep their organizations protected and available.
Table of Contents
How a DDoS Attack Works
Every DDoS attack follows a deliberate process designed to overwhelm, exhaust, and disrupt. While tactics vary, the objective remains the same: render a targeted system or service unavailable by consuming its resources faster than they can recover.
According to Zayo, the average DDoS attack costs unprotected organizations $408,000 total, or $6,000 per minute.
- Zayo Group's Distributed Denial of Service (DDoS) Insights Report 2023
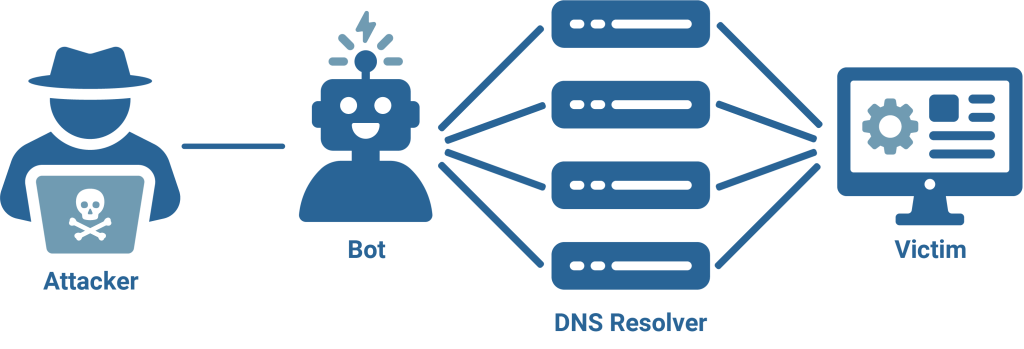
#1 - Building the Botnet
The attack begins with the creation of a botnet, a distributed network of compromised devices under an attacker’s control. Vulnerable IoT devices, routers, or unpatched servers are infected with malware that allows remote execution. Each infected system becomes a “bot,” ready to generate traffic on command. Large botnets, sometimes containing millions of devices, give attackers the scale needed to launch high-volume, globally distributed attacks.
#2 - Target Selection and Reconnaissance
Once the botnet is established, the attacker identifies the intended victim. During reconnaissance, they analyze the target’s network topology, exposed services, bandwidth capacity, and DNS infrastructure. This information helps determine the most effective attack vector, for example, whether to flood the victim’s DNS resolvers, exploit protocol weaknesses, or exhaust application resources.
#3 - Attack Execution
After reconnaissance, the attacker issues commands to the botnet, directing each compromised device to send requests toward the victim or its DNS resolvers. The surge of traffic overwhelms the target’s ability to process legitimate requests, resulting in slowed performance, connection timeouts, or complete outages. Depending on the scale and sophistication, these attacks can persist from minutes to several days, forcing victims to divert bandwidth and resources toward mitigation.
#4 - Sustained Disruption and Adaptation
Advanced adversaries continuously monitor the effectiveness of their attacks and adapt in real time. If defenders block one vector, such as TCP SYN floods, attackers may shift to application-layer (HTTP) or amplification-based techniques, using DNS or NTP resolvers to multiply traffic volume. This adaptive behavior makes static defenses ineffective and requires a shift to dynamic protection capable of rerouting or filtering traffic mid-attack.
The power of a DDoS attack doesn’t come from sophistication, but from scale, thousands or even millions of compromised devices acting in unison. What begins as a few infected systems can quickly grow into a weapon capable of disrupting entire networks, services, and supply chains.
Types of DDoS Attacks
Today’s DDoS landscape spans volumetric, protocol, application-layer, horizontal, and multi-vector attacks, each targeting different layers of the network stack and demanding a tailored, adaptive defense strategy.
Among these techniques, horizontal attacks have emerged as a key evolution, spreading low-intensity traffic across many endpoints or services to overwhelm distributed systems without triggering defenses.
Almost 30% of the total DDoS attacks mitigated by Akamai Prolexic were multidestination, horizontal DDoS attacks.
- According to Akamai
These are the most common and easiest to recognize. Volumetric attacks aim to consume all available bandwidth by flooding the target with massive amounts of data, often using amplification techniques to multiply their impact. Attackers may exploit services like DNS, NTP, or SSDP to reflect and amplify requests, producing traffic volumes that can exceed hundreds of gigabits per second.
Rather than overwhelming bandwidth, protocol-based attacks exhaust the resources of network devices such as firewalls, routers, and load balancers. Common examples include SYN floods, Ping of Death, and Smurf attacks. These exploit weaknesses in Layer 3 and Layer 4 protocols, especially TCP/IP, causing legitimate connection requests to fail.
Often the hardest to detect, these attacks mimic legitimate traffic while targeting specific applications or services. For example, HTTP floods and slow POST/GET attacks overload web servers by exploiting the resources used to handle each request. Because the traffic appears normal, traditional perimeter defenses may fail to distinguish it from legitimate user behavior.
Horizontal attacks differ from traditional floods in that they distribute low-intensity traffic across a wide range of endpoints or services instead of concentrating it on a single target. Each request may appear harmless in isolation, but collectively, they consume significant backend processing power and API bandwidth. This tactic is especially effective against cloud-based or microservice architectures, where distributed components share resources behind load balancers or shared APIs.
Modern adversaries increasingly combine multiple techniques into a single coordinated campaign. A multi-vector DDoS attack might begin with a volumetric flood to distract defenders while simultaneously launching an application-layer assault designed to bring down critical systems. This layered approach complicates mitigation and underscores the need for dynamic, automated defenses.
Each category of DDoS attack exploits a different layer of trust within the network, from raw bandwidth to application logic. Effective defense requires visibility across every layer and the ability to detect, respond, and adapt in real time.
Detection and Mitigation Strategies
Mitigating a DDoS attack begins long before an attack is underway; it starts with continuous visibility and proactive detection. Because modern DDoS campaigns often mimic legitimate user activity or blend across multiple vectors, early identification depends on strong baselining, behavioral analytics, and automated correlation. The faster an organization can detect abnormal traffic behavior, the more effectively it can contain and mitigate the impact.
Early Detection Through Visibility and Baselines
Effective DDoS detection relies on understanding what “normal” looks like. Security teams should establish detailed network baselines, including typical bandwidth consumption, connection rates, geographic traffic distribution, and protocol usage. Once those benchmarks are defined, continuous monitoring tools can flag deviations that signal potential attacks.
Network flow analysis, behavioral analytics, and deep packet inspection (DPI) technologies are key to distinguishing legitimate spikes, such as product launches or marketing events, from malicious floods. When combined with automated alerting and correlation across logs, firewalls, and SIEM data, these insights enable faster, more confident identification of DDoS activity.
Layered Mitigation Techniques
Because DDoS attacks target multiple layers of the OSI model, no single control can stop them. A layered defense, integrating both on-premises and cloud-based solutions, provides the most robust protection.
At the network perimeter, firewalls, intrusion prevention systems (IPS), and rate limiters can detect and filter malformed packets or excessive connection attempts. Application delivery controllers (ADCs) and web application firewalls (WAFs) defend higher layers by validating HTTP requests and throttling abusive behavior.
Beyond the perimeter, cloud-based scrubbing centers and content delivery networks (CDNs) absorb and redistribute large traffic volumes before they reach internal systems. These cloud defenses can scale dynamically, ensuring availability even during massive volumetric attacks.
Automation and Dynamic Response
Today’s DDoS campaigns evolve rapidly. Attackers frequently shift from volumetric to application-layer floods within minutes. Automation allows defenses to adapt at the same pace.
By integrating dynamic routing, adaptive filtering, and automated rate-limiting, organizations can respond in real time without manual intervention. Coupling these capabilities with live threat intelligence feeds enables systems to recognize known botnets and malicious IP ranges instantly. This reduces latency in mitigation decisions and ensures countermeasures evolve alongside the threat.
Resilience and Preparedness
Even the best technology can falter without well-rehearsed processes. Organizations should routinely test their defenses through simulated DDoS exercises and tabletop scenarios that evaluate both technical performance and communication workflows.
These rehearsals reveal bottlenecks, clarify escalation paths, and validate SLAs with third-party providers. The goal is operational resilience, maintaining uptime and customer trust even under attack.
Ultimately, effective DDoS defense combines visibility, layered protection, automation, and preparedness. Organizations that continuously monitor their networks, test their response plans, and integrate adaptive mitigation strategies can withstand even the most sophisticated attacks with minimal disruption.
Integrating DDoS Protection into Your Exposure Management Strategy
Defending against DDoS attacks requires more than reactive mitigation; it demands integration into a broader exposure management strategy. Availability risks are exposures just like unpatched vulnerabilities or misconfigured cloud assets. When overlooked, they create blind spots that attackers can exploit to disrupt critical services and operations.
By incorporating DDoS protection into a Continuous Threat Exposure Management (CTEM) framework, organizations can continuously identify where availability is most at risk, validate the effectiveness of existing defenses, and prioritize improvements based on business impact.
Through continuous assessment, validation, and optimization, security teams gain the visibility needed to anticipate disruptions, measure readiness, and ensure that availability is continuously protected.
FAQs About DDoS Attacks
What causes a DDoS attack?
A DDoS attack occurs when a network or website is intentionally overwhelmed with traffic from multiple sources, often through a botnet made up of compromised systems or IoT devices. The goal is to exhaust bandwidth, disrupt services, or force systems offline.
Can DDoS attacks be completely prevented?
No defense is foolproof, but layered security significantly reduces the risk. Combining firewalls, rate limiting, intrusion prevention systems, and cloud-based DDoS mitigation services helps absorb or filter malicious traffic before it reaches critical systems.
How do IoT devices contribute to DDoS attacks?
Many IoT devices lack proper security controls and ship with default passwords, making them easy to compromise. Once infected, they can be remotely controlled to send massive volumes of traffic during coordinated attacks.
What are the warning signs of a DDoS attack?
Unexplained network slowdowns, service interruptions, connection timeouts, and traffic spikes from unfamiliar IP ranges are common indicators. Real-time traffic analytics and monitoring tools can help detect these anomalies early.
How should organizations prepare for DDoS attacks?
Preparation starts with continuous visibility and testing. Establish response playbooks, perform stress-testing exercises, and work with cloud providers or ISPs that offer DDoS mitigation support. Regularly patching and securing IoT devices also limits the potential scale of an attack.
How does CTEM help organizations defend against DDoS attacks?
Continuous Threat Exposure Management (CTEM) brings DDoS resilience into the broader exposure management process. By continuously identifying and validating availability risks, from misconfigured firewalls to untested failover systems, CTEM helps organizations proactively strengthen their defenses and ensure that DDoS protection is treated as a continuous process.



