What Is Red Teaming? Understanding the Value of Real-World Attack Simulation
In cybersecurity, identifying vulnerabilities is just the beginning. The real test is whether those vulnerabilities can be exploited, and what happens if they are. That’s where Red Teaming comes in.
Red Teaming is the most rigorous form of security testing, designed to evaluate how an organization holds up against realistic, multi-stage attacks. Unlike standard penetration testing, which is often less rigorous and ends at technical vulnerabilities, Red Teaming pushes further, simulating the objectives, persistence, and adaptability of real-world threat actors. It’s a full-spectrum engagement that probes not only technical defenses but also human and procedural weaknesses.
In this article, we’ll explore what makes Red Teaming different, what a well-executed engagement looks like, and how organizations can use it to validate their defenses under pressure.
How Red Teaming Works
At its core, Red Teaming is adversary simulation. It’s designed to answer a simple but critical question: If a real attacker targeted your organization, how far could they get, and how long would it take for you to notice?
Red Team operations are goal-oriented and unrestricted. Rather than scanning for vulnerabilities in isolation, Red Teamers emulate full attack paths, from initial reconnaissance to exploitation, lateral movement, and final objective. This might involve breaching physical security, gaining initial access through phishing, escalating privileges, and exfiltrating sensitive data, all without tripping your defenses.
To simulate real-world threats, Red Teams use a broad set of tactics that blend technical skill with creative thinking. Some of the most common include:
- Social Engineering – Crafting phishing emails, voice calls, or even impersonation attempts to trick employees into granting access or revealing credentials.
- Initial Access Exploits – Leveraging exposed services, zero-day vulnerabilities, or misconfigured assets to establish a foothold.
- Credential Harvesting and Replay – Stealing usernames and passwords from memory dumps, insecure storage, or dark web leaks, then using them to move laterally.
- Privilege Escalation – Exploiting misconfigurations or vulnerabilities to move from a user account to domain administrator or root access.
- Lateral Movement – Hopping between systems, domains, or cloud environments to gain deeper access to the organization’s infrastructure.
- Command and Control (C2) – Establishing covert communication channels to remotely operate within the environment without detection.
- Objective Completion – Executing the final step in the kill chain, such as exfiltrating files, accessing sensitive data, or simulating data destruction.
Red Teaming Engagements are typically carried out over weeks or even months. The goal isn’t just to find security gaps; it’s to observe how your organization responds under pressure. Can your SOC detect a slow, stealthy attacker? Are incident response procedures followed? How long does it take to contain the threat?
It’s a true test of your defenses, one that uncovers what automated scans can’t.
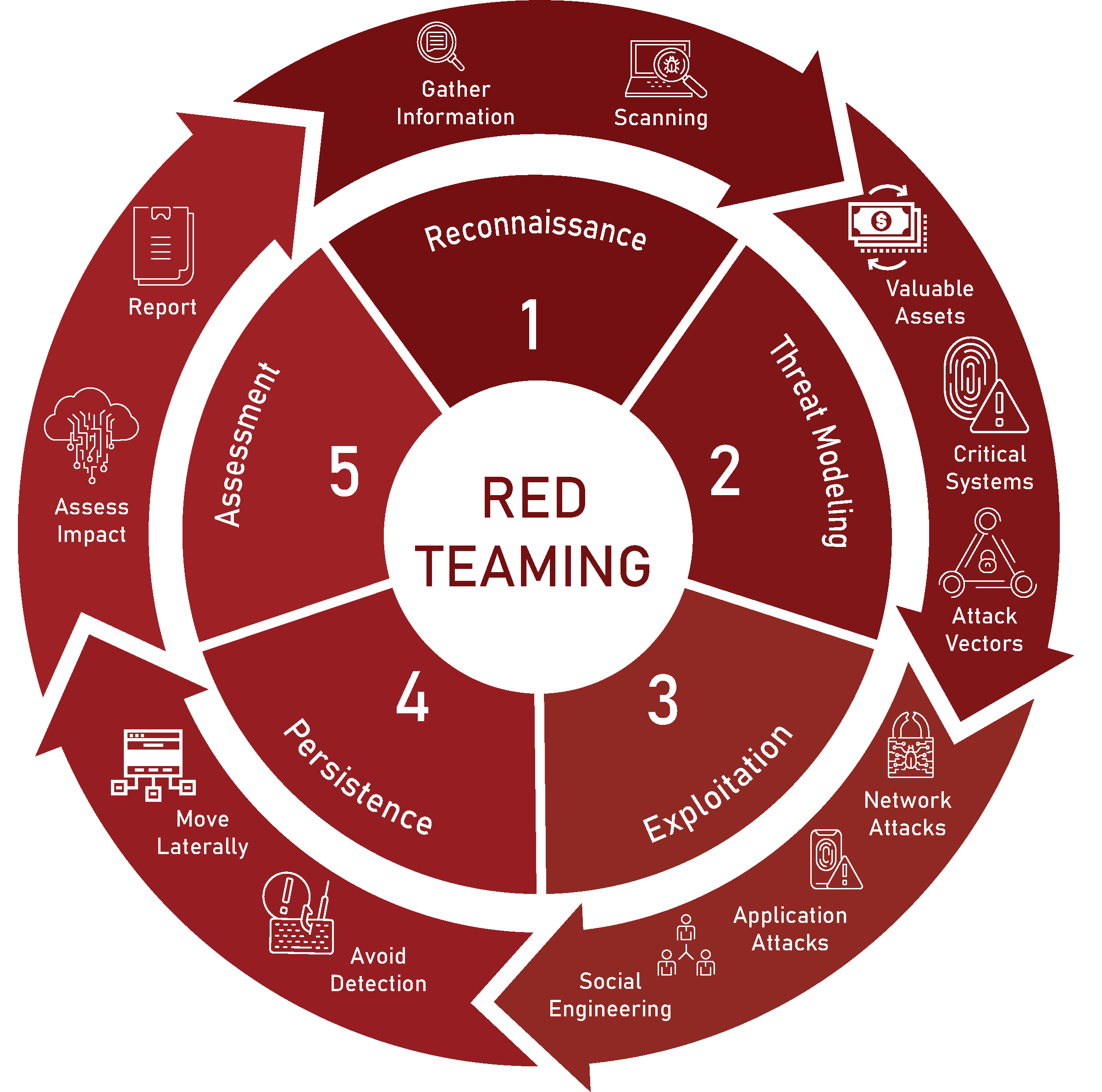
The Red Teaming Process
While every Red Team engagement is tailored to the organization’s goals, industry, and threat landscape, the process follows a deliberate structure designed to mirror real-world attacks.
At TrollEye Security, our Red Teaming process is built to be thorough, stealthy, and impactful, providing clarity not just on what could happen, but how to stop it.
The Red Team begins by gathering intelligence from publicly available sources, called OSINT. They collect everything from domain records to employee email formats, looking for any sliver of information that can be weaponized. Scanning helps map the attack surface, identifying live hosts, open ports, unpatched services, and cloud-exposed assets. At this stage, your organization is already under simulated surveillance, just as it would be in the early stages of a real-world breach.
Next, they translate that raw data into an attack strategy. They identify the most valuable assets, the critical systems that support them, and the plausible vectors of attack. Whether that’s a cloud identity misconfiguration, an exposed development server, or a susceptible executive assistant, the Red Team builds an adversarial roadmap that mirrors how a motivated attacker would prioritize and pursue access.
Armed with a plan, the Red Team begins its assault. They launch real-world attacks, phishing emails, password spraying, web app exploits, or direct network intrusions to breach defenses and gain initial access. This isn’t a theoretical simulation; it’s a controlled attack under strict engagement rules, designed to expose how far an intruder could get before being stopped.
Once inside, the Red Team works to maintain access and avoid detection. They escalate privileges, move laterally, and test your defenses from the inside. Whether it’s bypassing endpoint protections, pivoting through internal infrastructure, or quietly exfiltrating sensitive data, this phase puts your monitoring and incident response capabilities to the test.
After the operation concludes, you assess the real-world impact. If you use our Red Teaming Assessments, we will deliver a detailed report outlining our access paths, what went undetected, and which objectives were reached. After the report is delivered our red team will debrief with your team to walk through findings, remediation strategies, and steps to improve detection and response moving forward. The goal isn’t just to point out gaps, it’s to help you close them.
Red Teaming isn’t just about proving that a breach is possible; it’s about revealing how it would actually happen and whether your team is prepared to stop it. By following a structured, attacker-aligned process, Red Teams can expose the vulnerabilities that matter most: the ones that can be chained together and weaponized in the real world.
Can Red Teaming Be Automated?
The rise of advanced tools like Xbow has sparked a growing conversation: how much of Red Teaming can, or should, be automated?
Automation and AI can undeniably enhance certain aspects of a Red Team Engagement. Tasks like OSINT collection, exposed asset discovery, and even automated payload generation can now be done faster and at greater scale than ever before. These capabilities offer speed and efficiency, particularly in the early stages of an engagement.
But Red Teaming is more than a series of isolated technical actions. It’s about thinking like an adversary with a mission, adapting in real time, chaining together unexpected paths, and exploiting a mix of technical, human, and physical weaknesses. That level of improvisation and contextual judgment is where human Red Teamers remain irreplaceable.
What a Proper Red Teaming Assessment Looks Like
If you’re serious about testing your cybersecurity posture, Red Teaming offers more than just a checklist; it’s a full-spectrum stress test of your organization’s ability to detect, respond to, and contain real-world threats. But what does a well-executed Red Teaming Engagement actually look like?
To answer that, we’re presenting a real example of a Red Teaming Assessment we conducted for General Bank of Canada (GBC).
As a federally regulated Schedule I Canadian chartered bank, GBC had invested heavily in cybersecurity, deploying layered defenses, enhancing detection capabilities, and building out incident response plans. What they didn’t yet know was how well all of it would hold up under a realistic attack scenario.
So, they did what many organizations talk about but few execute properly: they ran a Red Team Assessment designed to simulate a real-world adversary. This wasn’t a routine penetration test; it was a full-spectrum adversarial simulation. Over the course of the engagement, our Red Team tested GBC’s defenses from every angle:
Reconnaissance and OSINT identified shadow IT assets, local vendors, and domain spoofing opportunities.
External and Internal Penetration Testing probed their digital infrastructure for exploitable vulnerabilities.
Targeted Phishing Campaigns assessed user awareness and response under social engineering pressure.
Physical Security Assessments included live intrusion attempts, with red teamers impersonating local vendors to test onsite defenses.
Dark Web Analysis was used to identify any data leaks, breach records, and stolen credentials relevant to GBC and its affiliates.
Incident Response Tabletop Exercises wrapped the engagement, testing their response to a simulated engagement built with real findings from the assessment.
Every step mirrored how an actual adversary might plan and execute an attack, from pretexting to privilege escalation to lateral movement, all while tracking what was detected and how fast internal teams responded.
The results were both validating and encouraging for GBC.
- Validated Investments – The assessment confirmed that GBC’s layered defenses were largely effective. Critical controls held up under pressure, preventing or slowing attack progression at several key points.
- Improved Response Readiness – Through simulated attacks and an IR tabletop, GBC’s team was able to gain a greater understanding of the threats they faced and how to improve their response strategy.
- Strategic Roadmap for Improvement – Beyond individual findings, the engagement delivered a clear, prioritized roadmap for refinement, spanning technical controls, physical safeguards, and procedural gaps.
The Red Team exercise conducted by TrollEye Security provided invaluable insights into our cybersecurity posture. The comprehensive approach combining dark web analysis, phishing campaigns, external penetration testing, physical security testing, and internal network assessments gave us a realistic view of our security posture.

Red Teaming Is the Security Reality Check Every Organization Needs
In today’s threat landscape, the question isn’t whether you have security controls in place; it’s whether they actually work when it matters most. Red Teaming provides that answer. It’s not about theoretical vulnerabilities or passive assessments. It’s about simulating real adversaries, testing every layer of defense, and validating your team’s ability to detect and respond under pressure.
Done right, Red Teaming delivers more than a list of findings. It offers proof, proof that your investments are effective, that your processes are resilient, and that your people are prepared. And when gaps are found, it provides a clear path to closing them.
At TrollEye Security, we’ve seen firsthand how Red Teaming transforms security programs from static to battle-ready. Whether you’re facing regulatory scrutiny, preparing for audits, or simply want to stay ahead of emerging threats, a properly executed Red Team Assessment is one of the most valuable tools at your disposal.
FAQs About Red Teaming
What is Red Teaming?
Red Teaming is the most rigorous form of security testing, a controlled, realistic simulation of multi-stage attacks that mimics the methods of genuine threat actors. It goes beyond standard penetration tests by pushing deeper into your systems, processes, and human elements to uncover how well your organization can withstand sophisticated attacks.
How does Red Teaming differ from traditional penetration testing?
While pen testing typically focuses on finding technical vulnerabilities within scoped systems, Red Teaming has a broader, goal-oriented approach. It uses unrestricted tactics, including social engineering and physical intrusion, to assess how far a motivated attacker could go. This approach reflects real-world attacks more accurately.
What happens during a Red Teaming engagement?
Red Teaming begins with reconnaissance and planning, gathering information with or without pre-authorization. The team then attempts to achieve specific objectives using realistic adversarial strategies, testing not just technology but human and procedural defenses. Once complete, findings are documented and transformed into actionable steps to strengthen your security posture.
Can Red Teaming be automated?
While certain phases, such as vulnerability scanning or exploitation, may be partially automated, Red Teaming relies heavily on creativity and adaptability. The human element, strategizing attacks based on evolving context, remains central to delivering meaningful insights.
How does Red Teaming fit within broader defense strategies?
Red Teaming serves as the adversarial test of your defensive readiness. By combining it with internal readiness exercises like blue teaming, or collaborative approaches like Purple Teaming, organizations can build a dynamic, resilient security ecosystem.



