What is Red Teaming?
It is important for modern organizations to integrate a practice known as Red Teaming—an approach that takes on the mindset of adversaries, employs their techniques, and tests an organization’s defenses against simulated real-world attacks. In this article we will explore Red Teaming’s methodologies and benefits
Red Teaming simulates real-world attacks to evaluate security defenses, uncover vulnerabilities, and strengthen overall security posture, it enhances vulnerability management and focuses on reconnaissance, exploitation, and data exfiltration. Collaboration between Red Teams and Blue Teams (Purple Teaming) is crucial, the future of Red Teaming includes addressing emerging trends like cloud security, IoT security, and AI/ML security. Red Teaming remains important for proactive security, compliance, and risk management.
What is Red Teaming
When it comes to securing an organization’s digital assets, traditional security assessments and measures can only go so far. They often fail to capture the ingenuity and sophistication of genuine cyber threats, leaving vulnerabilities undiscovered and defenses untested. This is where Red Teaming comes in, it’s an approach that goes beyond the superficial and takes on the persona of cybercriminals. It allows organizations to witness their vulnerabilities from the perspective of those seeking to exploit them.
Rooted in military exercises designed to challenge defense strategies, Red Teaming has found its place in cybersecurity, where the stakes are equally high. It simulates real-world attacks, evaluates an organization’s security posture, and uncovers hidden weaknesses that may have otherwise gone unnoticed. Adopting the mindset and tactics of adversaries, it exposes vulnerabilities, identifies gaps in defenses, and provides organizations with valuable insights into their security resilience.
We will dive deep into the intricacies of Red Teaming. We will explore its methodologies and its impact on vulnerability management. We will examine its execution and shed light on the collaboration between Red Teams and Blue Teams, called Purple Teaming, who work together to fortify an organization’s security infrastructure. By the end of this article, you will understand why it’s not just an exercise in simulation but a powerful catalyst for continuous improvement in cybersecurity.
The Origins of Red Teaming
To truly appreciate the essence of Red Teaming, we must first dive into its origins. The concept traces its roots back to military strategies and war gaming exercises, where opposing teams simulated attacks and defenses to test and refine their strategies. Over time, this practice transitioned into cybersecurity, where the battlefield shifted from physical landscapes to the digital domain.
Understanding the Mindset of Adversaries
At its core Red Teaming revolves around understanding the mindset of adversaries. It involves thinking like a hacker, analyzing motives, methods, and tactics. By adopting this perspective, organizations can gain valuable insights into potential vulnerabilities, allowing them to strengthen their defenses and minimize the risk of successful cyberattacks.
The Objectives of Red Teaming
The primary objective of a Red Teaming assessment is to expose weaknesses and vulnerabilities within an organization’s security infrastructure. It goes beyond the surface-level assessments conducted through vulnerability scanning or penetration testing and immerses itself in the art of simulated attacks. Red Teaming strives to identify blind spots, highlight overlooked vulnerabilities, and challenge the efficacy of existing security measures.
Simulating Real-World Attacks
It goes beyond theoretical exercises and simulates real-world attacks, mirroring the tactics employed by genuine threat actors. This approach allows organizations to experience the intensity and unpredictability of cyber threats in a controlled environment. By emulating these attacks, Red Teams provide organizations with a realistic assessment of their defensive capabilities, preparing them to face the ever-evolving landscape of cyber threats.
The Benefits of Red Teaming
Red Teaming offers a holistic security assessment that encompasses technical, procedural, and human factors. It evaluates the effectiveness of not only technical controls but also the organization’s response protocols and employee awareness. This comprehensive assessment helps organizations identify gaps and weaknesses across all layers of their security architecture.
It empowers organizations to adopt a proactive defense stance. By identifying vulnerabilities and weaknesses before adversaries exploit them, organizations can take preventive measures, strengthen their defenses, and minimize the impact of potential cyber incidents.
Its dynamic nature allows organizations to adapt their security strategies in real-time. As new attack techniques and trends emerge, Red Teaming exercises enable organizations to assess their readiness and adjust their defenses accordingly. This adaptability ensures that organizations stay ahead of evolving threats and continuously improve their security posture.
It assists organizations in effectively mitigating risks by exposing vulnerabilities and weaknesses. By identifying potential attack vectors, organizations can allocate resources more efficiently, prioritize security investments, and make informed decisions to safeguard critical assets and data.
It serves as a powerful tool for raising security awareness among employees and stakeholders. By simulating realistic attack scenarios and utilizing social engineering techniques, Red Teams provide valuable training opportunities. This awareness empowers individuals to recognize and respond effectively to potential threats, contributing to a security-conscious organizational culture.
Red Teaming involves a five step process and employs a variety of methodologies to simulate real-world attacks and evaluate an organization’s security posture comprehensively. These five steps are:
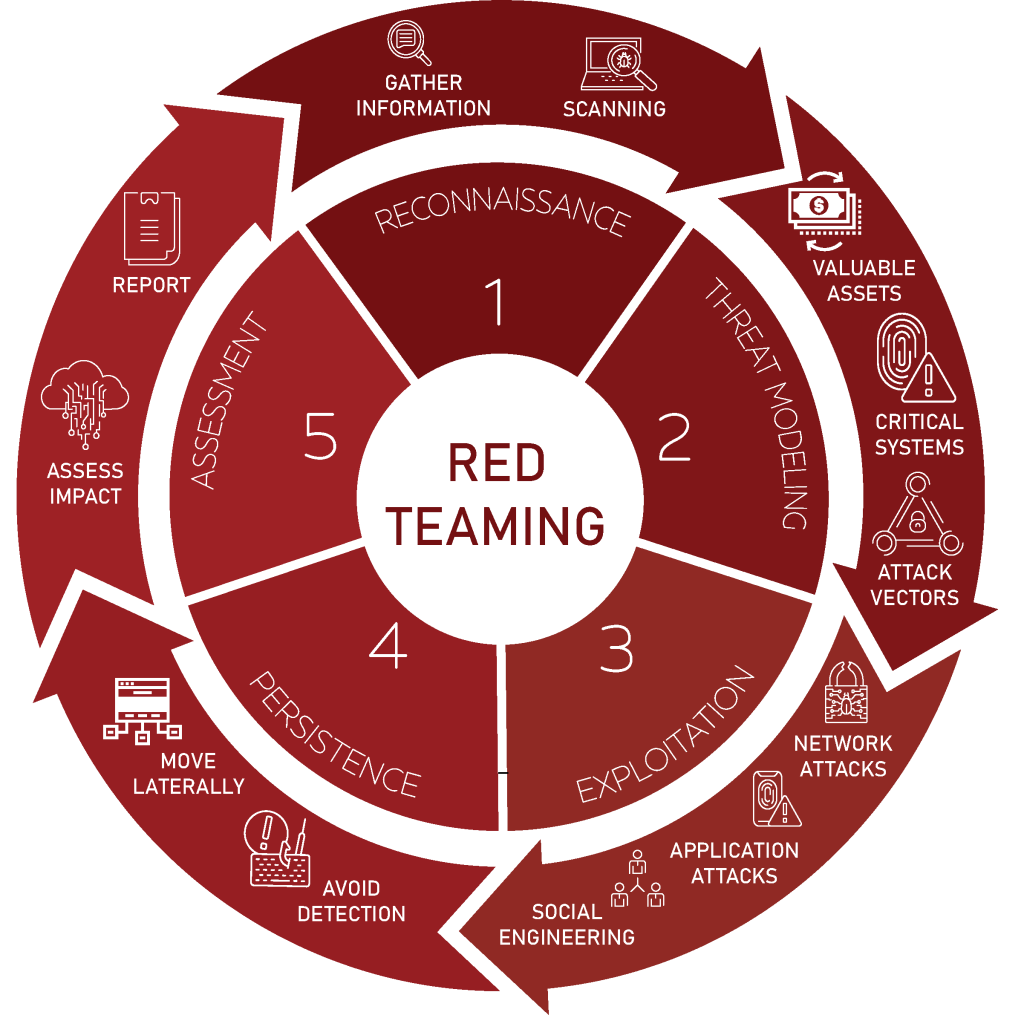
Red Teams start by gathering information about the target organization, its infrastructure, employees, and potential vulnerabilities. This phase involves open-source intelligence (OSINT) research, social engineering techniques, and network scanning to identify potential entry points.
They then analyze the gathered information to identify high-value assets, critical systems, and potential attack vectors. This helps prioritize the focus areas and tailor the simulations to address the specific security concerns of the organization.
Red Teams then employ various techniques to exploit identified vulnerabilities and gain access to systems or sensitive data. This may include network exploitation, application-level attacks, or social engineering techniques to trick employees into divulging sensitive information.
Once initial access is achieved, Red Teams explore the organization’s network, aiming to move laterally and gain deeper access to critical systems. They establish persistence by maintaining their access and evading detection, mimicking the techniques employed by sophisticated threat actors.
Then they simulate data exfiltration to demonstrate the potential impact of a successful breach. This helps organizations understand the repercussions of a security incident and evaluate the effectiveness of their incident response procedures.
Collaboration Between Red Teams and Blue Teams
Red Teaming exercises are most effective when there is a collaborative effort between Red Teams and Blue Teams (Purple Teaming). Blue Teams represent the organization’s defenders, responsible for maintaining and strengthening the security infrastructure. The collaboration between these teams enhances the overall security posture of the organization.
During Red Teaming engagements, Blue Teams actively defend against the simulated attacks. They analyze and respond to the tactics used, aiming to detect, mitigate, and neutralize the threats. This collaboration fosters knowledge sharing, allowing Blue Teams to learn from the techniques employed by Red Teams and refine their defenses accordingly.
The collaboration between Red Teams and Blue Teams extends beyond the engagement itself. Post-engagement debriefings and knowledge transfer sessions provide valuable insights to both teams. Red Teams share their findings, techniques, and recommendations, enabling Blue Teams to address vulnerabilities, enhance their incident response capabilities, and continuously improve their security measures.
Red Teaming and Regulatory Compliance
In today’s regulatory landscape, organizations are bound by various industry-specific compliance requirements. Red Teaming plays a vital role in helping organizations meet these regulatory obligations.
Payment Card Industry Data Security Standard: For organizations handling payment card data, Red Teaming can assist in validating compliance with PCI DSS. By simulating attacks targeting cardholder data environments, Red Teams can identify potential vulnerabilities and ensure that appropriate security controls are in place.
Health Insurance Portability and Accountability Act: Healthcare organizations must safeguard patient information as per HIPAA regulations. Red Teaming exercises can assess the effectiveness of security measures and help identify any weaknesses that may lead to unauthorized access or data breaches.
General Data Protection Regulation: The GDPR mandates stringent measures to protect the personal data of EU citizens. Red Teaming can aid organizations in assessing their compliance with GDPR requirements by identifying vulnerabilities that may compromise the security of personal data and providing recommendations for remediation.
Integration of Red Teaming Within Cybersecurity Frameworks
Integrating Red Teaming within cybersecurity frameworks enhances an organization’s overall security posture and complements existing security measures. Here are some key aspects to consider when integrating Red Teaming:
It provides valuable insights into the latest attack techniques and emerging trends. By integrating Red Teaming results with threat intelligence programs, organizations can enhance their incident response capabilities, fine-tune security controls, and proactively defend against evolving threats.
Red Teaming exercises serve as powerful tools for training employees and raising security awareness within an organization. By simulating realistic attack scenarios and employing social engineering techniques, Red Teams can educate employees about potential threats and how to respond effectively. This integration fosters a security-conscious culture and strengthens the human element of cybersecurity.
Red Teaming aligns with the principles of continuous improvement and risk management. By conducting regular exercises, organizations can identify vulnerabilities, assess the effectiveness of remediation efforts, and continuously improve their security posture. This proactive approach helps organizations stay ahead of emerging threats and mitigate risks effectively.
The collaboration between Red Teams and Blue Teams, known as Purple Teaming, is crucial for effective integration. Purple Teaming promotes knowledge sharing, facilitates the transfer of skills and insights, and strengthens the overall security infrastructure of an organization. By working together, Red and Blue Teams can enhance incident response capabilities, refine security measures, and fortify defenses.
Red Teaming goes beyond traditional security assessments by simulating real-world attacks, uncovering hidden vulnerabilities, and providing valuable insights into an organization’s security resilience. By integrating it within cybersecurity frameworks, organizations can strengthen vulnerability management, enhance regulatory compliance, and foster a proactive and resilient security posture. When conducted ethically and collaboratively, it becomes an indispensable tool for organizations seeking to safeguard their sensitive data and stay one step ahead of malicious actors in the ever-evolving cybersecurity landscape.
Implementing Red Teaming
Implementing Red Teaming within an organization requires careful resource allocation. While Red Teaming offers valuable insights and enhances security, it is essential to consider the associated costs and resource requirements.
Building an effective Red Team requires individuals with diverse skill sets and expertise in various areas of cybersecurity. Hiring or training personnel with the necessary knowledge and experience is crucial for conducting successful exercises.
Red Teaming exercises may require specific hardware, software, and specialized tools to accurately simulate real-world attacks. Ensuring that the Red Team has access to the necessary infrastructure and tools is essential for conducting comprehensive assessments.
Exercises should be planned and scheduled carefully to minimize disruptions to the organization’s operations. Adequate time should be allocated for the engagement, including reconnaissance, testing, analysis, and reporting phases.
Measuring the Effectiveness of Red Teaming Exercises
To gauge the effectiveness of exercises and justify the investment, organizations should establish metrics and evaluation criteria. Consider the following approaches:
Assess the impact of the identified vulnerabilities and the potential consequences of a successful attack. This evaluation helps determine the significance of the vulnerabilities and the effectiveness of the organization’s defenses.
Measure the organization’s security posture before and after Red Teaming exercises. Look for improvements in vulnerability remediation, incident response capabilities, and overall risk reduction.
Evaluate the effectiveness of Red Teaming exercises in raising employee awareness and improving their ability to detect and respond to potential threats. Assess the impact of training initiatives on the organization’s security culture.
Analyze the organization’s incident response performance during exercises. Measure response times, effectiveness in detecting and mitigating simulated attacks, and overall incident management capabilities.
By implementing these measurement techniques, organizations can assess the value and effectiveness of their investment in Red Teaming, demonstrate tangible improvements, and make informed decisions regarding future security strategies.
Red Teaming is an invaluable practice that enables organizations to evaluate their security defenses comprehensively, identify vulnerabilities, and strengthen their overall security posture. As technology advances and cyber threats evolve, Red Teaming will continue to play a crucial role in helping organizations navigate the complex cybersecurity landscape.



