How Are Our Dark Web Analysis Services Different?
Services Different?
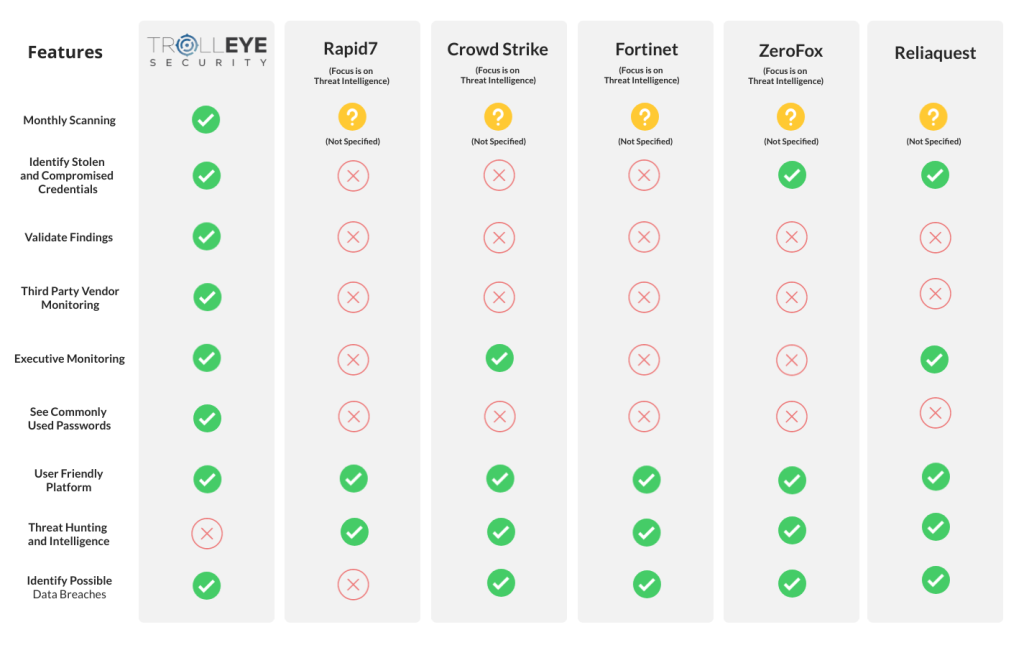
At TrollEye Security, we recognize the challenge in choosing the right cybersecurity solution. That’s why we have fine-tuned our Dark Web Analysis service to be a standout offering in the market. Our comparative analysis lays out a clear, feature-by-feature evaluation of how our services measure up against other top providers. We are the only B2B dark web solution that offers monthly scanning which allows us to identify stolen and compromised credentials, validation of those findings, executive monitoring, and third-party vendor monitoring — all essential in today’s threat landscape. With our chart you can compare our features with those of Rapid7, Crowd Strike, Fortinet, ZeroFox, and Reliaquest, many of whom focus on threat intelligence, while our focus is on analysis, identifying stolen and compromised credentials, monitoring executives and third-party vendors, and identifying possible data-breaches.
How Are Our Dark Web Analysis Services Different?

Learn More About Our Dark Web Analysis Offering
Upon evaluation, it's clear that our Dark Web Analysis services offer unparalleled value. We have designed it to be thorough in its capabilities and unmatched by other B2B dark web solutions. By integrating monthly scanning, third-party vendor monitoring, and the identification of compromised credentials, our Dark Web Analysis offering will make an excellent edition to your cybersecurity strategy.
As a crucial element of our Four Pillars of Cyber Risk Management strategy, Dark Web Analysis works with Penetration Testing, DevSecOps as a Service, and Managed SIEM to fortify your cyber defenses. While each pillar is powerful on its own, collectively they take your cybersecurity to the next level.
What Are The Four Pillars of Cyber Risk Management?
At TrolleyEye Security, we take a dynamic and proactive approach to cybersecurity. Our continuous security solutions work hand in hand with your existing defensive measures, enhancing your enterprise’s overall risk management. Our unique methodology provides deep insights into your network’s vulnerabilities, insights that you won’t find elsewhere. By applying our Four Pillars of Cyber Risk Management, we aim to detect, isolate, and remedy system weaknesses before they can be exploited.

Penetration Testing
When it comes to serious penetration testing, it can’t be a one and done philosophy that only runs testing on an annual basis. New risks and new forms of attack are constantly being developed by bad actors. Which is why we specialize in providing continuous penetration testing, also known as Penetration Testing as a Service (PTaaS), which we perform on either a quarterly, monthly, or weekly basis. As part of your overall enterprise risk management strategy, we offer a unique, continuous approach that gives you insight into your network security that can be obtained in no other way.
By continuously testing your systems, we can help you find, isolate, and correct weaknesses in your system before they’re exploited by criminals. Continuous penetration testing gives you an ongoing view of your security-posture, rather than just a look at one point in time. This allows your organization to continuously find and remediate vulnerabilities, to constantly improve your tactics, techniques and procedures (TTPs), and to improve your overall security posture.

Dark Web Analysis
As part of our penetration testing, we access and analyze dark web content to see if our clients’ data is no longer private. Based on our findings, you may be prompted to cancel credit card numbers, lock down your credit, and change critical passwords to prevent criminals from using that stolen information. By cutting off the use in advance, you can lighten the burden of responding to a data breach, reduce the associated costs, and give these criminals less incentive to try it again. Forward-thinking companies that are engaging our continuous penetration testing will benefit even more, as we will constantly be analyzing dark web data and notifying them immediately when we find breaches.

DevSecOps as a Service
We believe that security should be an inherent part of every aspect of software development. From design and coding, to testing and deployment. Our DevSecOps methodology emphasizes a proactive and continuous approach to cybersecurity, enabling organizations to identify and address vulnerabilities early on, rather than reacting to incidents retrospectively. By integrating security practices throughout the development lifecycle, DevSecOps ensures that security controls, risk assessments, and compliance measures are tightly woven into the fabric of your software ecosystem. This approach reduces the surface area for potential attacks, enhances code quality, and fosters a culture of security awareness among development teams.

Managed SIEM
At TrollEye Security we have expanded our product, Command Center, to include both Attack Surface Management and Managed SIEM capabilities, with it, we are able to perform Purple Teaming Engagements on your organization.
This revolutionizes the way organizations protect their digital assets by seamlessly integrating the proactive mindset of Purple Teaming with the robust capabilities of Managed SIEM. Making our Managed SIEM solution not just a reactive measure, but one that is used in an extremely proactive manner. But what exactly does this mean for your organization? It means that you are not just investing in a reactive security solution; you are empowering your cybersecurity defenses with proactive, adaptive, and highly effective strategies that stay one step ahead of potential threats.


Powered By Our SaaS Product, Command Center
All of our services are powered by our SaaS product, Command Center. It was originally built solely as a Penetration Testing Management Platform, that distributes findings to security teams based on their role. Since then, Command Center has gained Attack Surface Management and Managed SIEM capabilities turning it into a full blown, three-in-one, Cyber Risk Management Platform.
There are many ways your organization can use Command Center, the first way is simply by using our services; when you use our services your security team gains access to our platform. If you want to use Command Center to manage your own in-house penetration testing findings, then you can purchase an Enterprise License. And if you want to use Command Center under your own label, we offer a White Labeling License. Make sure to get a demo of our platform today!
