What is Purple Teaming?
While Red Teaming which is focused on offensive tactics, and Blue Teaming, which is focused on defensive measures, have their limitations when implemented separately, Purple Teaming bridges the gap by fostering collaboration, knowledge sharing, and joint efforts between Red and Blue Teams.
The essence of Purple Teaming lies in its ability to align offensive and defensive strategies creating a unified and proactive defense approach. By integrating the offensive mindset of Red Teams with the defensive expertise of Blue Teams, organizations gain a comprehensive understanding of their vulnerabilities and improve their ability to detect, prevent, and respond to cyber threats.
The Process of Purple Teaming
Through Purple Teaming, organizations conduct a cycle of meticulous planning, targeted cyber-attack simulations, and defensive responses, followed by a detailed analysis of the outcomes. This process encourages the continuous improvement of security measures, enabling the identification and remediation of vulnerabilities.
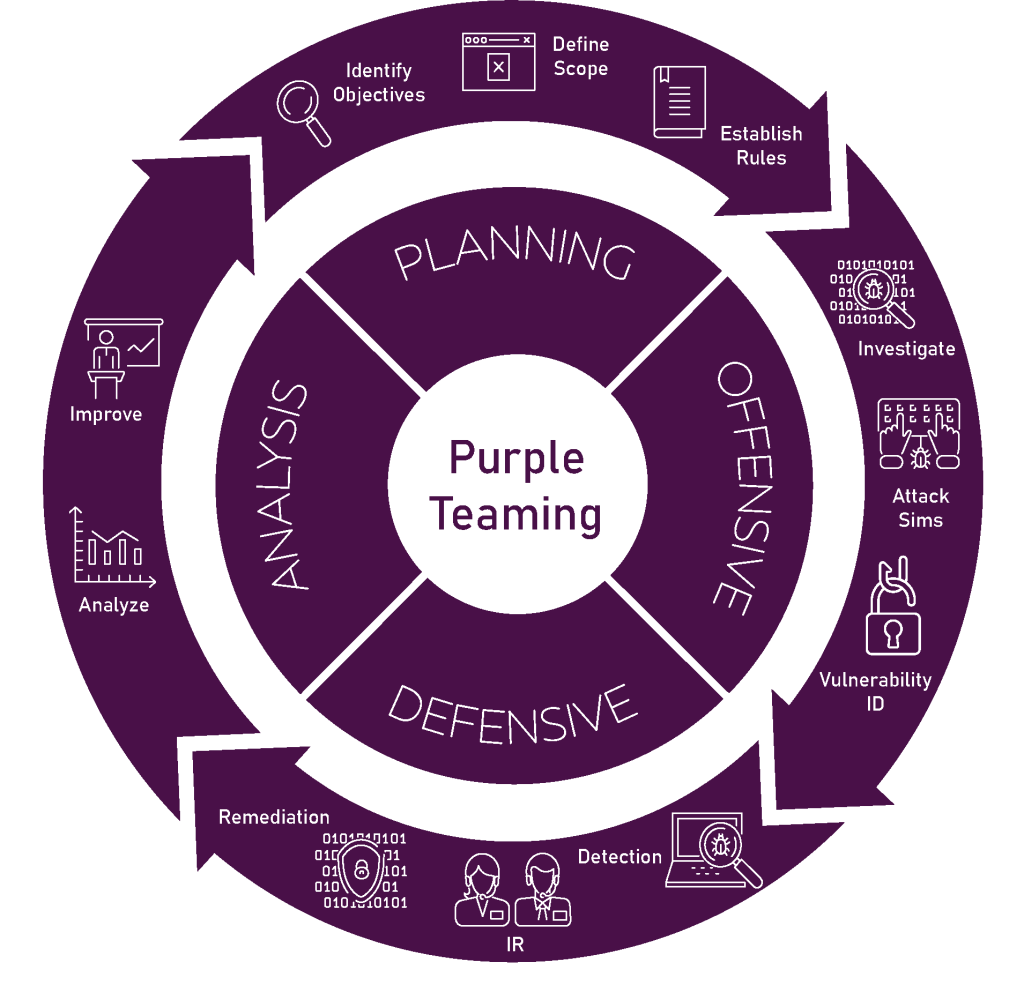
- Identify Objectives: This is the initial step where the Purple Team defines what they aim to achieve. Objectives may include improving detection rates, reducing breach impact, or enhancing response times.
- Define Scope: With clear objectives, the team sets the scope of the exercise, outlining which systems, networks, and assets will be included in the testing.
- Establish Rules: To maintain order and ensure no actual harm comes to the organization’s assets, rules of engagement are put in place. These rules determine how aggressive the Red Team can be and what actions the Blue Team will take in response.
- Investigate: The Red Team begins by gathering information on the target, identifying potential entry points and weaknesses that could be exploited.
- Attack Simulations (Sims): Using the data collected, the Red Team launches controlled cyber attacks against the organization, employing tactics and techniques reflective of real-world adversaries.
- Vulnerability ID: Throughout the offensive operations, the Red Team identifies and documents vulnerabilities, which will later be addressed by the Blue Team.
- Detection: The Blue Team uses various tools and strategies to detect the simulated attacks in real-time, aiming to identify and intercept the Red Team’s maneuvers.
- Incident Response (IR): In response to detected threats, the Blue Team executes incident response protocols to contain and mitigate the impact of the attacks.
- Remediation: Post-incident, the Blue Team works on addressing the identified vulnerabilities, patching up security holes, and strengthening the system against similar future attacks.
- Improve: Leveraging the insights from the analysis, the organization updates its security protocols, tools, and training to improve its defenses.
- Analyze: The improved strategies are then analyzed for effectiveness, ensuring that each iteration of the Purple Teaming process results in a tangible enhancement of security measures.
The Foundations of Purple Teaming
Purple Teaming builds upon the traditional Red Teaming and Blue Teaming methodologies, by combining offensive and defensive strategies organizations can achieve a more comprehensive understanding of their security posture. In this section we will talk about the origins and key principles that form the foundations of Purple Teaming.
Purple Teaming emerged as a natural evolution of Red Teaming and Blue Teaming methodologies. Red Teaming traditionally focused on simulating real-world attacks to expose vulnerabilities, while Blue Teaming emphasized defensive measures to detect and respond to threats. However these approaches often operated in silos lacking a cohesive collaboration, Purple Teaming bridges this gap by uniting offensive and defensive teams in a coordinated effort.
At its core lies collaboration, by working together Red Teams and Blue Teams can leverage their respective expertise, knowledge, and insights. Red Teams bring their offensive mindset emulating sophisticated attackers and uncovering vulnerabilities, while Blue Teams bring their defensive expertise analyzing and improving existing security controls. This collaboration enables a comprehensive assessment of an organization’s security defenses.
Purple Teaming aligns the objectives of Red Teams and Blue Teams ensuring they work towards a common goal, the focus is not solely on finding vulnerabilities but also on refining defensive measures to mitigate those vulnerabilities effectively. This alignment fosters a shared understanding of the organization’s risk landscape, enhances communication, and promotes a unified approach to addressing security gaps.
Purple Teaming creates an environment that encourages knowledge sharing and skill development, Red Teams and Blue Teams learn from each other gaining insights into the tactics, techniques, and procedures (TTPs) used by attackers as well as effective defensive strategies. This cross-pollination of expertise fosters continuous learning and empowers individuals to improve their skills in both offensive and defensive cybersecurity practices.
By combining offensive and defensive capabilities Purple Teaming enhances an organization’s threat detection and response capabilities, Red Teams simulate realistic attack scenarios allowing Blue Teams to test and validate their detection and response mechanisms in a controlled environment. This collaboration provides invaluable insights into the effectiveness of existing security controls and helps organizations refine their incident response processes.
Purple Teaming extends beyond technical aspects and aligns with an organization’s broader business objectives. By integrating cybersecurity into the overall business strategy Purple Teaming enables organizations to prioritize security investments, effectively allocate resources, and ensure that security measures align with the organization’s risk appetite.
A collaborative approach is foundational to Purple Teaming, aligning the offensive capabilities of Red Teams with the defensive expertise of Blue Teams, by fostering collaboration, knowledge sharing, and aligned objectives, it empowers organizations to achieve a comprehensive understanding of their security posture, improve threat detection and response, and align cybersecurity efforts with business objectives. In the following sections, we will explore the practical implementation and its benefits for organizations of all sizes and industries.
The Benefits of Purple Teaming
Purple Teaming is not just a theoretical concept it is a practical approach that organizations can implement to enhance their cybersecurity defenses, in this section we will explore the practical aspects of implementing Purple Teaming and the significant benefits it offers to organizations.
Effective collaboration and communication between Red and Blue Teams are crucial for the success of Purple Teaming, regular interactions such as joint meetings, debriefings, and knowledge sharing sessions foster a spirit of teamwork and create opportunities for cross-pollination of ideas. By maintaining open lines of communication Red and Blue Teams can collaborate in real-time, sharing insights, addressing concerns, and collectively working towards strengthening the organization’s security posture.
The core of Purple Teaming lies in conducting realistic attack simulations, Red Teams employ sophisticated tactics and techniques mimicking the strategies used by real-world threat actors to challenge the organization’s defenses. These simulations allow the organization to evaluate the effectiveness of its existing security controls, detect vulnerabilities, and identify areas for improvement. By emulating real-world attacks organizations can be provided with actionable insights to fortify their defenses.
Purple Teaming is an iterative process that involves continuous monitoring and feedback between Red and Blue Teams. Blue Teams actively monitor the simulated attacks, analyze the effectiveness of their defensive measures, and provide feedback to Red Teams. This feedback loop is invaluable in refining defensive strategies, enhancing incident response capabilities, and continuously improving the organization’s security posture.
One of the significant benefits of Purple Teaming is its ability to enhance an organization’s threat detection and response capabilities, by conducting realistic attack simulations Purple Teaming helps organizations identify gaps in their detection mechanisms, fine-tune their security controls, and improve incident response processes. This proactive approach empowers organizations to stay ahead of emerging threats, minimize response times, and effectively mitigate potential damage.
Purple Teaming also contributes to the overall security awareness and training within an organization, by involving both Red and Blue Team members in joint exercises, knowledge sharing, and skill development activities, organizations can create a culture of continuous learning and improvement. This collaborative environment fosters a deeper understanding of the evolving threat landscape, enhances individual skills, and promotes a security-conscious culture throughout the organization.
Implementing Purple Teaming can provide a significant return on investment for organizations, by proactively identifying vulnerabilities, fine-tuning security controls, and improving incident response capabilities, organizations can reduce the risk of costly data breaches, operational disruptions, and reputational damage. The upfront investment in Purple Teaming exercises is outweighed by the long-term benefits of enhanced security and minimized risks.
Purple Teaming can also assist organizations in meeting compliance and regulatory requirements, by conducting comprehensive assessments that align with industry standards and regulatory frameworks, organizations can demonstrate their commitment to security and compliance. Purple Teaming exercises provide valuable evidence of proactive measures taken to protect sensitive data and mitigate security risks.
Purple Teaming represents a paradigm shift in cybersecurity enabling organizations to leverage collaboration, knowledge sharing, and joint efforts between Red Teams and Blue Teams. The practical implementation of Purple Teaming leads to significant benefits including enhanced threat detection and response, improved security awareness and training, and a higher return on investment.
Purple Teaming offers a proactive approach to cybersecurity aligning offensive and defensive strategies to create a comprehensive defense strategy, by implementing it, organizations can fortify their security posture, identify vulnerabilities before they are exploited, and establish a culture of continuous improvement in cybersecurity.
Embracing the power of Purple Teaming enables organizations to stay one step ahead of adversaries, mitigate risks effectively, and safeguard their critical assets and sensitive data, by fostering collaboration and integrating offensive and defensive capabilities, Purple Teaming empowers organizations to navigate the complex cybersecurity landscape with confidence, resilience, and a proactive mindset. To learn more about Purple Teaming services, click here.



